+1(209) 348-9544
order@myessayservices.com
+1(209) 348-9544
order@myessayservices.com
![]() Are you in High School, College, Masters, Bachelors or Ph.D and need someone to help write your essay or research? We offer premium quality essay writing help. All our papers are original, 0% plagiarized & uniquely written by our dedicated Masters specialists. My Essay Services is an experienced service with over 9 years experience in research writing of over 97,000 essays over the years. You will receive a plagiarism check certificate that confirms originality for any essay you order with My Essay Services. Fill the calculator on your right to begin placing your order now!
Are you in High School, College, Masters, Bachelors or Ph.D and need someone to help write your essay or research? We offer premium quality essay writing help. All our papers are original, 0% plagiarized & uniquely written by our dedicated Masters specialists. My Essay Services is an experienced service with over 9 years experience in research writing of over 97,000 essays over the years. You will receive a plagiarism check certificate that confirms originality for any essay you order with My Essay Services. Fill the calculator on your right to begin placing your order now!

Introduction
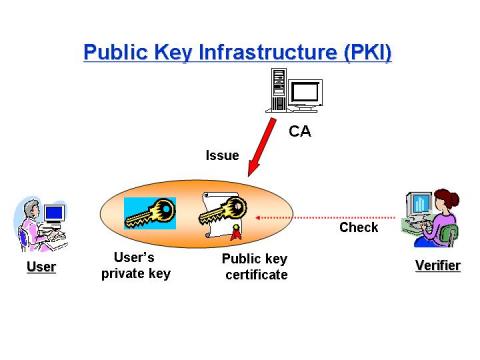 Public Key Infrastructure are systems applied in the public key identification and recognition of digital signatures in public environments thus enabling safe exchange of data and information over network platforms. “It has a number of security goals, such as accurate registration, which is the inability of a user to register an identity that does not belong to him or her, and identity retention, which is the inability of a user to impersonate an identity already registered to someone else.” Fromknecht et al (2014). They are applied in the management of certificates and keys. The utilization of PKI in the management of information within an organization ensures trust within the environments with which an organization operates in.
Public Key Infrastructure are systems applied in the public key identification and recognition of digital signatures in public environments thus enabling safe exchange of data and information over network platforms. “It has a number of security goals, such as accurate registration, which is the inability of a user to register an identity that does not belong to him or her, and identity retention, which is the inability of a user to impersonate an identity already registered to someone else.” Fromknecht et al (2014). They are applied in the management of certificates and keys. The utilization of PKI in the management of information within an organization ensures trust within the environments with which an organization operates in.
Fundamentals of PKI
The implementation of a transparent, automatic and usable PKI requires the utilization of number PKI fundamentals. An effective PKI is comprised of hardware, software procedures, policies and roles that act as a guide to the administrations and creation of the digitals certificates and keys. According to Slusky & Partow, “It integrates computer hardware and software, cryptography, information and network security, and policies and procedures to facilitate trust in distributed electronic transactions and mitigate the associated risks.” There exists a limited variation on both the server and clients sides in the use of PKI. In the administration of PKI, there must be a certificate authority who is the trusted party with which the services are provided thus ensuring that identities of all entities ranging from computers to individuals are effectively authenticated. A subordinate CA acts as the registration authority in the issuance of certificates that ought to be permitted by the root CA.
The PKI is also compromised of an effective database that stores issues concerning key and certificate requests. Private keys and certificates are stored on a certificate store which acts as the local systems. “A complete public key infrastructure is composed of several components which are: registration authority (RA), certificate authority (CA), security policy, PKI-enabled applications, distribution system, and certificate repository.” Albarqi et al, (2015).
Purpose in organizations
According to Ramadan et al (2016), “the public key infrastructure (PKI) is more compatible with the modern generations due to the superior communications features.” Firms ought to consider a number of factors in the implementation of PKI within business operations. The organization or individuals involved should be willing to take advantage of digital signatures and encryption in order to utilize the systems within the business. The user does not necessarily have to understand the techniques and approaches being employed within these systems in the provision of digital signatures and encryption services. Transparency is an important constraint that ought to be taken into consideration while utilizing these systems.
PKI in signing software
PKI systems have been effectively incorporated into an organization’s operations thus facilitating improved customer services, reduces costs of operations, smoothing of business processes. In addition to the ensuring trust during information sharing and storage, PKI will ensure that management of digital identities inventory, self-registrations, enrollment services and secure roaming and authentication of the PIN.
Companies can apply PKI signing software to identify the identity of the software such as those owned by the company. For example, software developed by a particular company could be signed in such a way that shows the ownership of the software by the enterprise. It can also be used to sign software being applied within a company thus eliminating access among individuals who do not have the authority to assess and utilize the software usually over the network. They are also used within the firms to ensure forms and electronic signing of software.
Public and In-house CAs
Internal CA is advantageous in that it facilitates easy management of the systems as they do not depend on external certificate sources. Moreover, they can be integrated effectively with minimal costs into an active directory within an organization. However, it might be too challenging to implement internal certificate authority (CA) as compared to an external CA. Overhead management for internal CA is usually higher than that of external CA with limited trust existing among the external parties.
External CA is advantageous in that they can be applied in different environments for accountability and security. External CA tends to capture the trust of external parties. Examples of external CAs include Thwate and Secure-Net. A major disadvantage of these is that they are less flexible when it comes to management, expansion and configuration of the certificates. Moreover, organizations will require purchasing external CA in order to effectively integrate them into an organization’s operations.
Conclusion
The rising technology has called for integration of PKI into an organization’s operations usually to enhance management of keys and certificates. Organizations ought to take into consideration a number of factors while implementing the systems into firms operations. PKI enhances the identity or authentication assurance among other parties in addition to ensuring confidentiality on the information being exchanged.
References
Albarqi, A., Alzaid, E., Al Ghamdi, F., Asiri, S., & Kar, J. (2015). Public Key Infrastructure: A Survey. Journal of Information Security, 6(1), 31.
Enaw, E. E., & Check, N. (2014, November). Public Key Infrastructure Deployment in Cameroon's Public Administration. In Proceedings of the 2014 Conference on Electronic Governance and Open Society: Challenges in Eurasia (pp. 26-29). ACM.
Fromknecht, C., Velicanu, D., & Yakoubov, S. (2014). A Decentralized Public Key Infrastructure with Identity Retention. IACR Cryptology ePrint Archive, 2014, 803.
Ramadan, M., Du, G., Li, F., & Xu, C. (2016). A Survey of Public Key Infrastructure-Based Security for Mobile Communication Systems. Symmetry, 8(9), 85.
Slusky, L., & Partow-Navid, P. Federal Public-Key Infrastructure.
Tan, S. Y., Yau, W. C., & Lim, B. H. (2015). An implementation of enhanced public key infrastructure. Multimedia Tools and Applications, 74(16), 6481-6495.
 We have all heard or even read about the identity theft stories involving individuals who mysteriously lose their credit cards or their social security numbers. These individuals take a long time and huge sums of money out of their pockets while straightening out the mess they found themselves in. In some instances, these individuals also lose great deals or even all of their life savings (Stickley, 2009). Below is one story that takes identity theft to a completely new level.
We have all heard or even read about the identity theft stories involving individuals who mysteriously lose their credit cards or their social security numbers. These individuals take a long time and huge sums of money out of their pockets while straightening out the mess they found themselves in. In some instances, these individuals also lose great deals or even all of their life savings (Stickley, 2009). Below is one story that takes identity theft to a completely new level.
Rivera Gertrudis of Allentown, Pennsylvania, has no clue how and when his birth certificates and Social Security number were stolen. But his conscience tells him that it can be about-twenty five years ago when, he worked as a young man serving as a fruit picker in the groves of oranges in Florida. As a Puerto Rican native and, therefore, the United States citizen, he had to provide his Social Security number as well as show his birth certificate each day when attending the fields (Hoffman & McGinley, 2010).
It seems; someone got his information and; as a result, Getrudis Rivera suffered many years of financial frustration since the Internal Revenue Service as evading to report his earned income pursued him. He also had his history of credits strewn with statements of late settlement of accounts he did not eve open at the first place. Greater nightmare for him came recently during his visit to Elm Street when he was informed that he was being prosecuted for child support by a maternal grandfather of an eleven-year old girl who was born to a woman he had never met (Hoffman & McGinley, 2010).
According to investigations made for the case, the Illinois Department of Public Aid informed Rivera's current employer that he had an automatic deduction of $146 every month from his salary for child support. Complexity emerged in relation to the case, with the Illinois investigators unveiling that Rivera Getrudis and another man called Juan Contreras shared the same identity. They eventually realized that two different men were using similar Security Service number for tax filings. Juan Contreras was allegedly using Rivera's identity even to obtain bank loans, driver's license and credit cards (Hoffman & McGinley, 2010).
Identity theft is a great problem that is affecting many people each day. That is why learning how to evade it is vital. Having knowledge on how to avoid identity theft makes one’s identity more protected. The more individuals know how to protect their identity, the less they are exposed to identity theft. Protecting identity theft begins with managing one’s personal information sensibly and carefully.
Attaining this can only be by carrying essential documents with you; this will minimize the chances of losing your documents. Also be careful when you are asked out confidential information over the phone as identity thieves might call, posing as government or banks agencies. Lastly, your trash can be the thieves’ treasure. Always shred your credit card offers, receipts, returned checks and bank statements before throwing it away (Stickley, 2009).
Having someone’s identity stolen has severe consequences in terms of money and other unfavorable consequences associated with their identity. For instance, identity thieves will drain their victim’s bank accounts, sell their properties, get away with their investments and defraud them out of their money before they find out. In addition to getting away with their money, identity theft can ruin their victim’s credit records; make piles of deceitful debts, lead to false arrests and even imprisonment (Stickley, 2009).
The high increase in cases of identity theft globally has coincided with similarly rapid advancement in innovation and technology. In reaction to the dominance of such criminal activities, a number of international companies have risen to involve solely in the practice of restoring damage done to individuals who have experienced stolen identities (Stickley, 2009). The companies include TrustedID, Lifelock, ID Watchdog and Identity Guard; which all work in ensuring the identity of individuals is safeguarded.
References
Hoffman, S. K., & McGinley, T. G. (2010). Identity theft: A reference handbook. Santa Barbara, Calif: ABC-CLIO.
Stickley, J. (2009). The truth about identity theft. Upper Saddle River, N.J: FT Press.
Browse More Essay Topics 24/7/365 Support 11+ Yrs in Essay Writing Pay for Quality not Quantity Score that A+ Grade
Affordable Papers
Research Paper for Sale
Cheap Research Papers
Buy Term Papers
Buy Research Paper
Write My Paper
Buy an Essay
Cheap Essay Writer
Write my Essay
Thesis Help
Dissertation Help
Paper Writing Service
Pay for Homework
Pay for Research Paper
Do My Essay for Me
Pay for Essay
College Papers for Sale
Do My Homework for Me
College Essays for Sale
Buy Research Papers Online
Buy College paper
Client: "(Berlin, G.K., CA)"
Topic title:"Leadership shortfalls in Blue Chips"
Discipline: "Economics"
Pages: 5, (APA)
" Awesome, the writer delivered it as required by the professor. They also sent me a plagiarism & grammar report Wow!. I was worried about how the essay would turn up but this is exactly what wanted. Thank you and will be back with a longer essay"
Accounting Research Papers
Business Research Papers
Communication Research Papers
Computer Science Research Papers
Economic Research Papers
Film Studies Research Papers
Finance Research Papers
Geography Research Papers
History Essays
Psychology Research Papers
Political Science Research Papers
Nursing Research Papers
Mathematics Essays
Management Essays
Literature Essays
Law Essays
World Affairs Essays
Technology Essays
Sociology Essays
Science Essays
Religion Essays
+1(209) 348-9544
Terms
Privacy
Sitemap
Frequently Asked Questions
0% Plagiarism Guarantee
Money Back Guarantee
Revision Policy
