+1(209) 348-9544
order@myessayservices.com
+1(209) 348-9544
order@myessayservices.com
![]() Are you in High School, College, Masters, Bachelors or Ph.D and need assistance with your technical, computing sciences research paper? All you need is to ask for essay help written by a specialist in your academic field. When you buy an essay from us, we offer you an original, nil plagiarized and unique paper written by a dedicated writer who is PhD or Masters qualified. MyEssayServices.com is an experienced service with over 9 years experience having delivered over 83,000 essays over the years.
Are you in High School, College, Masters, Bachelors or Ph.D and need assistance with your technical, computing sciences research paper? All you need is to ask for essay help written by a specialist in your academic field. When you buy an essay from us, we offer you an original, nil plagiarized and unique paper written by a dedicated writer who is PhD or Masters qualified. MyEssayServices.com is an experienced service with over 9 years experience having delivered over 83,000 essays over the years.

 Hacking is a hobby or profession of working with computers (O'Farrell, 2002). It involves breaking into computers. That is gaining access to other people’s computers without their awareness. Computer hacking is the process of making attempts gain or successfully gaining, unauthorized access to computer resources. It is a technique where intelligent people have an easy access to other people’s computer resources without their permission (O'Farrell, 2002). Computer hacking involves stealing data and information from other people’s computers or through the network without prior knowledge of the owner. It is the practice of modifying computer hardware and software aiming at accomplishing a goal outside the creators’ purpose of the system. Hackers are individuals involved in computer hacking. There are different reasons that motivate hackers. Some of the reasons motivating hackers include; profits challenge and as well protect (Strebe, 2006).
Hacking is a hobby or profession of working with computers (O'Farrell, 2002). It involves breaking into computers. That is gaining access to other people’s computers without their awareness. Computer hacking is the process of making attempts gain or successfully gaining, unauthorized access to computer resources. It is a technique where intelligent people have an easy access to other people’s computer resources without their permission (O'Farrell, 2002). Computer hacking involves stealing data and information from other people’s computers or through the network without prior knowledge of the owner. It is the practice of modifying computer hardware and software aiming at accomplishing a goal outside the creators’ purpose of the system. Hackers are individuals involved in computer hacking. There are different reasons that motivate hackers. Some of the reasons motivating hackers include; profits challenge and as well protect (Strebe, 2006).
Computer hacking is most common among teenagers and young adults. However, there are also old hackers. Many hackers are true buffers to systems and computer software who enjoy learning more about computer work and consider computer hacking as an art (Strebe, 2006). They mostly enjoy learning different programming methods and expert their knowledge on one computer programming style which they use in their hacking process (O'Farrell, 2002). Among these types of hackers, they use their knowledge as a real life application of solving their problems and as well demonstrating their skills other than harming other people. There are different types of hackers and different methods used by hackers to attack a system stealing unauthorized information. The essay will focus on the different types of hackers (Strebe, 2006).
As stated earlier, hacking is an art. Before learning the types of hackers, it is important to learn the different methods used by hackers while attacking a system. Methods used by hackers comprise of either taking control over server (terminal to a network) or crashing the system. Phishing is the most common method used by hackers (O'Farrell, 2002). It is another type of key logging where the user lands to a website created and resembling the legitimate website. Once the user enters his passwords, they enter to the hacker’s mail box. This method makes personal information vulnerable to an easy access since the hackers will have a direct access to the passwords of important sites. This hacking method is commonly used in online banking and as well website hacking (Strebe, 2006).
Another method used in computer hacking is spoofing and SQL injection. Spoofing involves hacking computers through the network (O'Farrell, 2002). It entails sending packets with anticipated acknowledgements through the network aiming at gaining access to computer files and making computer passwords vulnerable. Through spoofing, a hacker is able to predict and obtain passwords to computers in the network. On the other hand, SQL injection, a method used by hackers, involves exploiting security vulnerability occurring in the database of the application layer. Similar to spoofing method, SQL injection is only Achievable when the hacker has access to the network. The hacker uses SQL commands to get into the network and as well system where he acquires privilege rights that he uses to attack computers in the network (Jordan, 2008).
Viruses and worm is another method used by hackers while attacking a computer. Viruses and worms are self-replicating programs attaching themselves in other programs (viruses) and as well in the machine (worms) (O'Farrell, 2002). These programs affect the normal functioning of the computer by making attempts of shutting down networks. Achieving this is through flooding computers with massive amounts bogus traffic. Emails are highly in sending worms and viruses to target computers and servers. Through this method, injecting a computer with viruses and worms, makes their password vulnerable to attack by unauthorized people thus making it possible for exploiting personal information and as well files saved in the computer (O'Farrell, 2002).
Back doors, also called loopholes, are another method applied by hackers to access information in personal computers through the network (O'Farrell, 2002). Through this method, hackers get access to networks through exploitation of the back doors administrative shortcuts, configuration errors and easy passwords. Hackers gather information on these back doors using bots (computerized searches). This method highly gives hackers access to personal information in personal computers through the network (O'Farrell, 2002).
A Trojan horse, which is among the latest methods used by hackers, is a method where hackers attach Trojan horses to other programs (Strebe, 2006). They give hackers a direct access to personal computers since they cause all break-ins. This method gives hackers remote access to the computer when the user downloads and activates Trojan horses (Jordan, 2008). This software has the capability of having full control over a system, and personal computer and a hacker can remotely control the whole system (Jakobsson, 2012). In addition, cookie theft is another method used by hackers in getting remote access to personal computers and as well systems. Through this method, hackers use remote software of accessing cookie saved in computers taken from different sites and as well computer information saved in the form of cookie in the browser. This is another remote access method used by hackers while exploiting personal computers and as well administrative systems.
Lastly, hackers gain remote access to computers and systems through whaling and denial of service. This method entails getting passwords of accounts used in controlling a system and as well user accounts in the personal computers (Jordan, 2008). On the other hand, denial of service involves attacking a network through flooding the router with unnecessary packets leading to its failure. It gives hackers an easy access to network and therefore access to computers in the network. Once a hacker has an access to the network, he can easily track files and information shared through the network thus exploiting the information (Strebe, 2006).
Computer hacking, described as an art, has different execution methods (Jakobsson, 2012). These methods used by hackers makes computer hacking a high threat to information saved in computers and as well information conveyed through the computer system. After understanding the different methods used by hackers, we have a close analysis of the different types of hackers and hacking.
Black hat hacking is the most common type of hacking and considered as the most dangerous type of hacking. Black hacker (cracker or dark side hacker) is an individual involved in this type of hacking. Black hat hacking uses different channels of exploiting personal information and as well files saved in computers (Jakobsson, 2012). A black hacker uses his knowledge and skills for a negative (criminal) intent. Some examples of black hacker activities are cracking bank passwords aiming at making transferences to their personal accounts, stealing information aimed with a purpose of selling the information into the black market and lastly attacking computer network (systems) of an organization with an aim of making money and interrupting with their performance (Strebe, 2006).
Through black hat hacking, crackers have become representatives of hackers in around the world. Their activities cause social misfits among many people following their criminal nature. Once a black hacker has an access to a system, he takes advantage of the vulnerability of the system where he destroys files and steals some of the files for their personal gain. Black hat hacking activities have an impact on future performance of the attacked system (Jordan, 2008). Once the black hacker gets a remote access to the target system, he manipulates the configurations used through deletion of settings and as well resetting information shared through the system. Black hackers share the back doors of a given system and network to other hackers without notifying the victim. This has a negative impact on the victim as different hackers without the owner’s awareness easily execute the system’s loopholes. This makes black hacking the most malicious and dangerous type of hacking.
White hat hacking is the other type of hacking. This is a positive type of hacking. In this type off hacking, a hacker, employed by an organization, tests the vulnerability of the organization’s information and security of the network. White hat hacking involves determination of the vulnerability of an organization’s network (Strebe, 2006). White hackers are individuals involved in this type of hacking. White hackers use the different methods of hacking with an aim of accessing an organization’s delicate information. White hackers are not criminal in nature. This implies that they do not have intent intentions towards information collected through their setting. It is a type of ethical hacking with no negative impact on the performance of the organization. On the other hand, white hacking does not pose threats to personal information stored and shared through the network.
White hackers have a responsibility of reporting on the loopholes and vulnerability of an organization’s network. Therefore, white hacking aims at dealing with black hacking. That is the responsibility of white hackers is to determine the possible loopholes prone to use by black hackers (Jordan, 2008). Unlike black hacking, white hat hacking is partly legal. That is white hackers have prior permission from the target users of the system. White hackers have a high level of programming and computer networking skills. An example of white hat hacking is cyber-crime investigations. A white hacker does not share loopholes of a given sites and organization’s system to other hackers since their role is to help an organization secure the possible loopholes.
The third type of hacking is grey hat hacking. This type of hacking involves individuals between white and black hacking concepts (Jakobsson, 2012). That is grey hacking may have both legal and illegal purposes. Grey hat hackers are individuals involved in this type of hacking. Grey hackers use their skills in order to prove that they can accomplish a determined feat. Unlike other hackers, grey hat hackers do not involve themselves in hacking with an aim of making money. Grey hat hacking is a form of white hat hacking where the hacker acts unethically (Strebe, 2006). Grey hat hacking mostly takes place when a hacker, employed as a legit network security administrator, finds an opportunity of gaining access to company’s data and steals the data. In addition, a white hat hacker may turn to be a grey hat hacker when he detects vulnerability of a system and fails to report it to the employer. Grey hat hacking does not impose a great threat to an organization’s information. Lastly, cases of grey hacking may also arise when a white hat hacker detects a vulnerable loophole in an organization’s system and network but offers to correct the threat at a fee (Jakobsson, 2012).
The other type is elite hat hacking. Elite hacking involves individuals considered as experts in their line of work. Elite hackers are responsible for discovering new exploits. Among this type of hacking, they develop methods used in penetrating to an organization’s systems and acquiring relevant information regarding the organization (Jordan, 2008). They test the credibility of methods used by other hackers and determine the most effective methods used in attacking different sites. Therefore, elite hacking does not have a significant immediate threat to an organization’s system and network. However, elite hackers give other hackers new methods of attacking systems and computers (Jakobsson, 2012). Elite hackers do not have the interest of exploiting information and organization’s loopholes, but they engage in determining new methods for attacking the secure systems and networks of different organizations. Unlike other hackers, in elite hacking, after hackers develop a new method of hacking a system, they also develop a new method of dealing with the new hacking method. Therefore, elite hacking is a hacking style highly significant in the society (Jordan, 2008). This is because; it not only equips black hackers with new methods of attacking systems but also equips white hackers with new methods of dealing with black hacker attempts.
Script kiddie hacking is another hacking type that involves individuals with minimal hacking skills. Unlike black, white and elite hacking, script kiddie hacking involves the use of pre-packaged automated tools developed by other hackers. This implies that their hacking skills have a basis on other hackers. Script kiddie hacking entails breaking into computer systems with minimal pre-knowledge on computer security and hacking skill. This hacking style highly uses software other than codes in the hacking process. The difference between a script kiddie hacker and other hackers is that the former does not have a vast understanding on hacking and as well neither determines security vulnerabilities of a computer nor creates scripts and programs used by other hackers.
Blue hat hacking is another hacking style used by system developers. As with this hacking type, an individual outside computer firm gets the responsibility of bug testing a system before its launching. This hacking type is common in computer system developers (Jordan, 2008). It aims at determining possible exploits before launching the system. Microsoft, one of the computer consulting firms, use blue hat hacking before it launches its computer systems to the market. After locating possible exploits in the system, efforts of closing the exploits start (Jakobsson, 2012).
The last type of hacking is hacktivist hacking. It involves using technology aiming at announcing social, political and religious ideas to different people through the network. This type of hacking affects people within the same network. Hackivist hackers use denial of service method of hacking while exploiting a network (Jordan, 2008). These hackers do not have interests in stealing and having access to information in computers but aim at spreading their ideas to other people through the network. They have a negative impact on the network by flooding the network with packets conveying their message and ideas.
Depending on the target sites of hackers, there are the following hacking styles. Password hacking involves determining passwords used in accessing information or bypassing set password of securing some information and files (Jakobsson, 2012). Password hacking is through email password hacking, windows password hacking and bios password hacking. Password hacking gives hackers’ access to data and information through cracking the set passwords. Credit hacking is another hacking method that entails hackers having access to online bank accounts where they alter with the details transferring money to their accounts.
Hackers have both positive and negative impact on networks and computer systems. Black hackers have a use their hacking skills negatively (Jordan, 2008). However, in some cases, competing businesses use black hat hackers to gather information on the strategies used by their competitors. Therefore, organizations use black hacking while gathering information on other businesses. Both white hacking and blue hat hacking have a positive impact on organizations using them. This is because both white and blue hat hackers help organizations in closing possible loopholes used by black hackers (Jordan, 2008).
In conclusion, it is quite clear that there are different methods of computer hacking. In addition, there are different types of hackers who execute the different hacking methods. Hackers do their work for different reasons. Some hackers hack computer systems for fun while others hack these systems to steal important information. On the other hand, some hackers hack systems aiming at destroying their enemies’ computer work during wars and some hack to notify other people their thoughts and ideas. Therefore, hacking is an art done for different purposes. Network hacking has a negative impact on routing devices and as well people using the network. This is through the flooded packets and denial of service. More so, hackers can easily inject packets shared through the network with worms and viruses leading to poor performance of computer systems and as well network devices. Quality of service of a network faces a negative effect following the denial of service and flooded packets.
References
Jordan, T. (2008). Hacking: Digital media and technological determinism. Cambridge, UK: Polity Press.
Jakobsson, M. (2012). The death of the internet. Hoboken: John Wiley & Sons.
Strebe, M. (2006). Network Security JumpStartTM: Computer and Network Security Basics. Hoboken: John Wiley & Sons.
O'Farrell, N. (2002). Hack proofing XML. Rockland, Mass: Syngress Media.
 A virtual team is a group of people distributed over different geographical areas. In other words, a virtual team can be described as a group of people who are working across the boundaries of the business organization. Management of a virtual team is remotely done (that is there been centralization of managers and decentralization of team members). There is the strengthening of activities by communication technology. Virtual team members are usually under minimal supervision. Management of virtual teams has faced critics from different researchers. These teams, characterized by their dispersion and reliance on technology mediated methods of communication. They are different from face-face communication since they do not have face-to-face supervision and meetings. There is determination of performance by the nature of the members. Performance of the virtual teams is one key factor that has received a lot of attention within the last few years. Many researchers have consistently disintegrated factors considered having an influence on performance of management. Virtual teams are necessary for the performance of the business. Success of a virtual team influences the overall performance of the organization. The paper is a research whether a well thought adjustment in the method of communication; team building and ways of resolving conflicts are requisite for a successful virtual team.
A virtual team is a group of people distributed over different geographical areas. In other words, a virtual team can be described as a group of people who are working across the boundaries of the business organization. Management of a virtual team is remotely done (that is there been centralization of managers and decentralization of team members). There is the strengthening of activities by communication technology. Virtual team members are usually under minimal supervision. Management of virtual teams has faced critics from different researchers. These teams, characterized by their dispersion and reliance on technology mediated methods of communication. They are different from face-face communication since they do not have face-to-face supervision and meetings. There is determination of performance by the nature of the members. Performance of the virtual teams is one key factor that has received a lot of attention within the last few years. Many researchers have consistently disintegrated factors considered having an influence on performance of management. Virtual teams are necessary for the performance of the business. Success of a virtual team influences the overall performance of the organization. The paper is a research whether a well thought adjustment in the method of communication; team building and ways of resolving conflicts are requisite for a successful virtual team.
While designing a virtual time, the process of communication used for the interaction between managers and the members of the virtual team is necessary. Establishment of a clear team structure depends on the interaction between members (Kossler, 1996). According to researchers, establishment of a clear team structure enables the team to succeed. Some reports that, despite face-to-face meetings with the managers being effective, virtual meetings with team members through electronic communication methods such as emails and telephone can also improve the performance and effectiveness of the virtual team. Empowerment of virtual teams depends on the structure of virtual teams. Informing all members about the changes in the organization are essential in creating a clear team structure where all organization leaders are aware of the changes taking place in the organization. Effectiveness in a virtual team depends on the technology-mediated communications. In addition, effective virtual team highly depends on technology while carrying out its tasks. This implies that virtual meetings between team members and leaders are more effective than face-to-face interactions while carrying out their tasks.
Learning network, communities of practice and web-based interest groups do not transform a group of people into a virtual team. An effective virtual team described as a group of people working in an organization characterized by geographic dispersion and use of technologically mediated communications. Technologies such as telephone, faxes, e-mail and video conferences are very crucial in a virtual team’s management. This is an indication that leaders of successful virtual teams highly depend on technology methods of communication other than face-to-face meetings with members. Tasks that require especially instructions are best carried out using video calls. Leaders of virtual teams should be able to learn the best method of communication suitable for team.
Communication with team leaders using electronic methods is important in ensuring that there is completion of activities within the expected time. In addition, it is essential in ensuring that members are informed on the changes within the organization. Effectiveness of a virtual team depends on how virtual the team is. The degree of reliance on the use on electronic communication increases virtuality of the team. Teams relying on electronic communications are more virtual as compared to other teams that rely highly on face-to-face meetings with their leaders. Teams that do all their work through e-mails, text messages and teleconferences often do not have face-to-face meetings with their leaders. Virtual teams are at a high possibility of producing high-quality and innovative business solutions when the members of the team remain independent on each other and depend on technology mediated methods of communication (Kossler, 1996). Success of a virtual team is attributed to the ability to apply knowledge from one domain to the other. On the other hand, there is a consideration of reduced cost of coordination in a virtual team. For the success of a virtual team, adjustment of the communication process is a requisite for a successful virtual team.
Virtual teams rely highly on the effectiveness of communication (Kossler, 1996). This is influenced by the skills of the leader play an essential role in producing solutions towards dealing with the existing barriers and problems. This suggests that the communication adjustment is critical for a virtual team to succeed. Communication adjustment aims at dealing with upcoming challenges encountered while in the virtual team dealing. Emergent leaders play an essential role in virtual teams. These leaders are described as heavy contributors towards communication taking place in their virtual teams. In addition, they are responsible for initiating new ideas, expressing their opinions and as well asking questions during meetings. It is through their contributions that grant them an opportunity to be better placed as compared to other leaders in a virtual team. Emergent leaders are dynamic. As a result, their virtual teams tend to be more successful as compared to other teams. This can be attributed to their dynamic nature in decision making and expression of ideas. As a result, it is quite clear that the adjustment of communication in a virtual team is a requisite towards success of a virtual team (Kossler, 1996).
Goals are targets set by leaders of the team. As with other teams, virtual teams have goals that act as measures of performance. Setting up a strong team that is goal oriented promotes success of a virtual team (Haywood, 1998). Team building exercises are requirements in establishing goals. A successful virtual team is attained after an agreement on the team’s timetable, agreement in personal responsibilities and as well accountability. Prior to duty sharing, agreements are made in the virtual team. Unlike in a face-to-face training, in a virtual team, is often conducted virtually. However, for a successful virtual team, initial stages of team building should be done face-to-face. Team building is a critical stage towards a successful virtual team. Training is one requisite of a successful team building. Engaging members of a virtual team into some team building activities is critical in ensuring that the set goals of the organization are met. Team building training, helps the individual team members to build trust with their colleagues. Cohesiveness of in a virtual team is linked to team building training.
The nature of team building activities is one characteristic of a successful virtual team. Social activities such as eating and drinking are used by managers as team building activities (Haywood, 1998). Team building activities in a virtual team are carried out electronically where video clips are sent to managers. In addition, online activities such as discussion of the book and completion of exercises can be used as team building activities. According to the article by Jill Nemiro, Michael Beyerlein and Lori Bradley: a toolkit for collaborating across boundaries, a case of Jarvenpaa and others are given an example on how team building creates conditions that create trust among the members. He highlights that graduate students from different parts of the globe were invited to work on geographically distributed teams. A team building intervention was initiated. This was aimed at exchanging information on the skills related to the projects and as well motivation to the team effort. On the other hand, work and study habits were part of the team intervention. As soon as the team members posted the personal information in the website, team members and administrator had access to the information shared (Armstrong, 1996)? This contributed to trust between the team members. As team members, involving in team building activities not only creates trust among members but also creates a stronger bond between the members and leaders. Successful team members have a trait of engaging the members in team building activities. It is quite clear that team building is a requisite of a successful virtual team (Haywood, 1998).
Virtual teams are prone to conflicts. Conflicts within a virtual team range from personal conflicts to goal conflicts. As a team leader, dealing with these conflicts is essential. Successful team leaders have mechanisms of dealing with the conflicts before they affect the prevailing relationship between the team members (Armstrong, 1996). In a virtual team, conflicts have both negative and positive effects. Unlike in a face-to-face team, virtual teams’ conflicts are easy to manage. This is because in a virtual team, there is no much interaction between the members. However, when conflicts arise in the virtual team, leaders act as moderators towards the conflicts. Leaders have the role of making their members aware of sharing their viewpoints. However, the discussion on the conflicts should remain enclosed to the issue at hand (Wilson, 1994). This is aimed at preventing members from threatening each other. In addition, leaders to the virtual teams have the role of ensuring that they lay more emphasis on team identity. Strong team identity is another characteristic of a successful virtual team. Members are cohesive and committed to the team’s goals. This suggests that for the goals of a virtual team to be attained, dealing with conflicts as a leader influences the performance of the team (Haywood, 1998).
Successful virtual teams in an organization have a description of effective global network. This suggests that the teams have few struggles in understanding their roles as compared to face-to-face teams. Distribution of team members also has an effect while solving conflicts. According to the article, leading one another across time and space, exploring shared leadership functions in virtual teams by Marissa and Christopher, majority and minority influence result from an uneven distribution of ideas while dealing with conflict within the team members (Wilson, 1994). They continue to highlight that unnecessary conflicts bring about separation in a virtual team. Failure is one result of conflicts within a virtual team. Coordination challenges are faced by leaders when there are conflicts in the virtual team. As a result, leaders of a successful team act as mediators towards conflicting members. This suggests that leaders in a virtual team should have diplomatic methods to deal with conflicts arising between the team members (Haywood, 1998).
Despite the success attributed to the virtual teams by organizations, conflicts arising from team members can result to failure of the team. In addition, failure of team members knowing each other can contribute to the failure of the team (Wilson, 1994). In order to deal with conflicts within the team; it requires the leaders to come up with a harmonizing plan. On the other hand, the success of these virtual teams is dependent on conflict solving techniques used in the team (Haywood, 1998). As with Wilson, J.M., George, the authors of the chapter give a description of dealing with these conflicts among members. They highlight that while dealing with conflicts between the team members, it requires the leaders to have the basic reasons behind the conflict (Wilson, 1994). In addition, the authors highlight that success of a virtual team can be determined by method of dealing with conflicts. This is an implication that success of a virtual team depends on conflict solving techniques within a virtual team. Therefore, dealing with conflicts is a requisite for the success of a virtual team (Wilson, 1994).
While leading a virtual team, there are some essential tools that the leader needs. The manager of a virtual team has full impact towards the success of a virtual team. According to Haywood, he states that communication of a virtual team is critical. He states that this is not only important while carrying out tasks while in the team but also important while dealing with conflicts among team members. While leading a virtual team, a manager has the role of ensuring that all team members are trained with the technology process used. This suggests that changes within the medium of communication while in the virtual team have to be made aware to the members before its implementation (Haywood, 1998). Haywood describes a successful virtual team as a team that has met the communication requirement. He states that a successful team has its team members able to communicate effectively with each other (Armstrong, 1996).
In addition, while considering team building, it plays a role in establishing a successful virtual team. Haywood concludes his argument on successful virtual teams by highlighting the impact it has to the virtual team. He highlights that a successful virtual team is based on goals set aside before tasks are shared between the members. While acting as a remote manager, the manager has a great task in ensuring that team members have met the basic standards before they are enrolled into the team. Unlike in the face-to-face teams, a virtual team has the author of the receiver of the information being in control over the information. This is in contrast with face-to-face meetings where the sender of information has control over the message sent. This has an implication that adjustment of communication plays a critical role in ensuring that virtual team’s goals are met. Reports over the result of an adjustment of communication and team building have been given by researchers. Team building as well has been highlighted to be requisite for a successful virtual team (Haywood, 1998).
Success of a virtual team is dependent on individual effort of team members. While comparing face-to-face teams to virtual teams, there are some differences depending on individual efforts. This is according to an article on face-to-face versus computer mediated communications. Face-to-face teams are more efficient than virtual teams. However, a well-planned virtual team can be more efficient than the face-to-face communication teams. This is according to research made on the performance of virtual teams. Tasks that do not require socio-emotional interactions are best done using virtual teams than while using face-to-face teams. This suggests that the performance of virtual teams is dependent on the nature of the task (Bordia, 1997). In addition, the author of the article outlines that an effective virtual team is determined by the nature of communication media that are used. He states that communication medium used in a virtual team affects its effectiveness (Bordia, 1997). Adjustment of method of communication used in a virtual team plays an important role as the different tasks require different mediums of communication. Methods of communication used in a virtual team are determined by the tasks that the team will be handling (Haywood, 1998). Leaders of a virtual team have the role of ensuring that adjustment of the method of communication is done depending on the change in nature of tasks handled by the team.This implies that adjustment to communication is a requisite for a virtual team (Wilson, 1994).
Planning meetings is complicated in a virtual team since team members are dispersed over a wide geographic region. In a virtual team, planning for meetings should be done after consultations with the team members. Some conflicts in virtual teams arise as a result of sharing of tasks in a virtual team. Leaders of a virtual team should be aware of the skills that their members have regarding to the task carried out by the team (Wilson, 1994). This is one method of dealing with conflicts that arise from sharing of tasks. In addition, leaders should make the team members free to share their experiences while working in the team. A successful virtual team is characterized by leaders who make their members free to share their experiences while working in different geographical areas (Haywood, 1998). This implies that communication in a virtual team is vital. On the other hand, successful team leaders are described by their ability to solve conflicts in the virtual team. Conflict solving in a virtual team is crucial as it ensures that the initial trust among team members prevails. Sharing of information in a virtual team and responding to a message is another solution towards conflicting team members. This is an implication that conflict solving, and adjustment to communications are requisites for a successful virtual team (Wilson, 1994).
Qualitative analysis on successful virtual teams shows that these teams highly depend on the decisions made by the leaders. This implies that the leader’s decisions play a significant role towards the success of the virtual team. This is based on research aimed at exploring the antecedent of trust in global virtual teams. Research shows that an individual’s propensity to trust has a positive effect to the individual’s trust in the team (Jarvenpaa, 1998). Choice of team building activities is determined by the interaction between the team leader and the nature of tasks handled by the team. While carrying out these activities, the performance and effectiveness of virtual team members is improved. Team leaders make decisions on behalf of the team members (Haywood, 1998). As a result, they have full control over the performance of the team (Wilson, 1994). A successful virtual team is described as a team that has leaders who are good in decision making. Wrong decisions made by team leaders affect the team negatively. Communication of the decisions made by the leaders is done electronically in a virtual team. This suggests that team building is a requisite for a successful virtual team (Armstrong, 1996).
Virtual team leaders have a role of ensuring that they handle a basic team strategy before approaching the strategies of the virtual team. Managers of virtual teams are encouraged to have a heavy communication between team members to ensure that the members do not have a feeling of isolation (Wrdell, 1998). Successful virtual teams are characterized by the ability to use some strategies by the management. Strategies used by successful virtual teams are aimed at dealing with conflicts that arise among members of the team. In addition, these strategies are aimed at maintaining a good rapport with the team members. Strategies in a virtual team are communicated to the members during meetings. In a virtual team, videoconferencing is used to communicate strategies to the members. Conflicts in a virtual team are best solved using a strategic approach. This suggests that communication and solving conflicts are requisites for a successful virtual team (Haywood, 1998).
Since there is no strict supervision in a virtual team, their performance is dependent on the nature of the members. A successful team is described to have members who are responsible and as well able to carry out their tasks without being supervised by their leaders. Leaders of virtual teams play an important role in ensuring that members in a virtual team are responsible. This is done during team building. While recruiting team members, different standards should be set. Standards range from personal skills and as well responsibility in terms of carrying out their tasks. This suggests that the performance of virtual teams is dependent on the nature of team members. That is team building is a requisite for a successful virtual team (Haywood, 1998).
As from the research paper, it is quite clear that success of a virtual team leadership is dependent on some factors. These factors influence the performance of virtual teams. Adjustment to communication affects the performance of virtual teams. Virtual teams are highly dependent on technology mediated methods of communications. Successful virtual teams are defined by their ability to adjust to adjustment of communication. Adjustment of communication is determined by the nature of tasks being handled by a virtual team. Technology mediated methods of communication influence the nature of the team. On the other hand, team building influences the nature of a virtual team. Activities involved in team building build up trust among team members. Decisions during team building impact the performance of virtual teams. In addition, these activities are essential in ensuring that members learn the goals and targets of the company Successful teams are characterized by coordination of members. Lastly, dealing with conflicts in a virtual team influences the success of a virtual team. Successful virtual teams are characterized by the ability to solve conflicts among members. Dynamic virtual team leaders are attached to successful teams. Therefore, adjustment to communication, solving conflicts and team building are requisite for a successful virtual team.
References
Haywood, M. (1998). Managing virtual teams: Practical teachings for high-technology project managers. Boston: Artech House Publishers, 210 pages.
Armstrong, D. J., & Cole, P. (1996). Managing distances and differences in geographically distributed work teams. In S.E Jackson & M.N. Ruderman (Eds), Diversity in work teams: Research paradigms for a changing workplace (pp. 187-215). Washington, DC: American Psychological Association.
Barua, A., Ravindran, S.,& Whimston, A.B (1997). Coordination in information exchange between organizational decisions units. IEEE Transactions on Systems, Man, and Cybernetics: Part A. Systems and Humans, 27, 690-698
Bordia, P. (1997). Face-to-face versus computer mediated communication: A synthesis of the experimental literature. The journal of Business Communication, 34, 99-121
Kling, R. (1996). Social relationships in electronic forums. Hangouts, salons, workplaces and communities. In R. Kling (Ed), computerization and controversy: Value conflicts and social choices (2nd ed.,pp. 426-453). san Diego, CA: Academic Press, 961 pages
Kossler, M.E., & Prestige, S. (1996). Geographically dispersed teams Issues & Observations, 16(2/3), 9-11
Jarvenpaa, S.L., Knoll, K., & Leidner, D.E. (1998). Is anybody out there? Antecedents of trust in global virtual teams. Journal of Management Information Systems, 14(4), 29-64
Wrdell, C. (1998, November). The art of managing virtual teams: Eight lessons. Harvard Management Update, pp.4-5.
Wilson, J.M., George, J., Wellings, R.S., with Byham, W.C (Eds). (1994). Virtual teams in virtual organizations: A look at the future. Leadership trapeze: Strategies for leadership in team-based organizations (pp. 249-264). San Francisco: Jossey-Bass, 286 pages.
Journal: CMS WIRE
Article: How Hackers Can Use Facebook, Google to Crash Your Website
Author: Noreen Seebacher, April 28, 2014
Link: http://www.cmswire.com/cms/customer-experience/how-hackers-can-use-faceb...
Summary
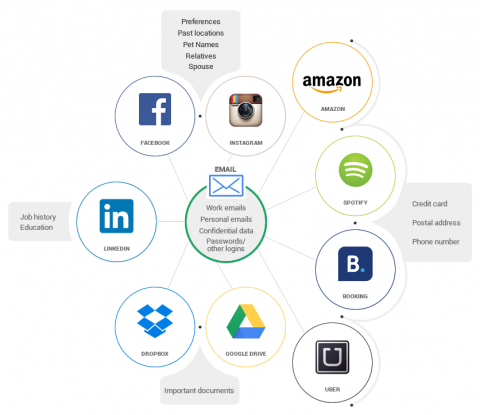 The author of the article highlights on how hackers use social media sites in their execution of cyber-attacks. He states that, through exploitation of these social media sites, hackers have a privilege of performing distributed denial-of-service (DDoS) attacks. Through these attacks, hackers are getting the opportunity of penetrating their target websites. According to the article, the hacking through social media channels is serious since it is easy in its execution and as well through its execution; there are huge volumes of traffic generated. Due to the huge traffic generated it would be devastating to the target sites (Seebacher, Apr 28, 2014 ).
The author of the article highlights on how hackers use social media sites in their execution of cyber-attacks. He states that, through exploitation of these social media sites, hackers have a privilege of performing distributed denial-of-service (DDoS) attacks. Through these attacks, hackers are getting the opportunity of penetrating their target websites. According to the article, the hacking through social media channels is serious since it is easy in its execution and as well through its execution; there are huge volumes of traffic generated. Due to the huge traffic generated it would be devastating to the target sites (Seebacher, Apr 28, 2014 ).
The author highlights that cyber threats are everywhere and hackers are using bugs in penetrating their target websites. Unlike in earlier hacking methods, Facebook and other social media traffic bug does not end wait for website users to visit these websites physically. Apparently, hackers hide behind social media site’s bandwidths. On the other hand, when a hacker intends to attack a server of an enterprise, they subject the traffic volumes to the server. This makes the server and the website prone to penetration due to the huge amounts of data (Seebacher, Apr 28, 2014 ).
The author later highlights on the importance of a company protecting itself from these attacks stating that it can be a measure of being responsible for their delicate data. More so, he states that companies can protect themselves from social media bugs attacks by blocking Facebook and Google’s user agents. The author highlights that limiting the number of tags in their websites can be a measure of avoiding this attack. More so, eh proposed that users could disable third parties that fetch notes and information on their websites (Seebacher, Apr 28, 2014 ).
I believe that in order to avoid DDoS attack, while transmitting their information through their network, they can add, “Request IP” in the information header. Considering the rise in cybercrimes, there is a need of dealing with possible threats subjected to servers and as well websites. This is in order to avoid huge traffics in form of bugs from social media sites.
References
Seebacher, N. (Apr 28, 2014 ). How Hackers Can Use Facebook, Google to Crash Your Website. CMS WIRE.
Browse More Essay Topics 24/7/365 Support 11+ Yrs in Essay Writing Pay for Quality not Quantity Score that A+ Grade
Affordable Papers
Research Paper for Sale
Cheap Research Papers
Buy Term Papers
Buy Research Paper
Write My Paper
Buy an Essay
Cheap Essay Writer
Write my Essay
Thesis Help
Dissertation Help
Paper Writing Service
Pay for Homework
Pay for Research Paper
Do My Essay for Me
Pay for Essay
College Papers for Sale
Do My Homework for Me
College Essays for Sale
Buy Research Papers Online
Buy College paper
Client: "(Berlin, G.K., CA)"
Topic title:"Leadership shortfalls in Blue Chips"
Discipline: "Economics"
Pages: 5, (APA)
" Awesome, the writer delivered it as required by the professor. They also sent me a plagiarism & grammar report Wow!. I was worried about how the essay would turn up but this is exactly what wanted. Thank you and will be back with a longer essay"
Accounting Research Papers
Business Research Papers
Communication Research Papers
Computer Science Research Papers
Economic Research Papers
Film Studies Research Papers
Finance Research Papers
Geography Research Papers
History Essays
Psychology Research Papers
Political Science Research Papers
Nursing Research Papers
Mathematics Essays
Management Essays
Literature Essays
Law Essays
World Affairs Essays
Technology Essays
Sociology Essays
Science Essays
Religion Essays
+1(209) 348-9544
Terms
Privacy
Sitemap
Frequently Asked Questions
0% Plagiarism Guarantee
Money Back Guarantee
Revision Policy
